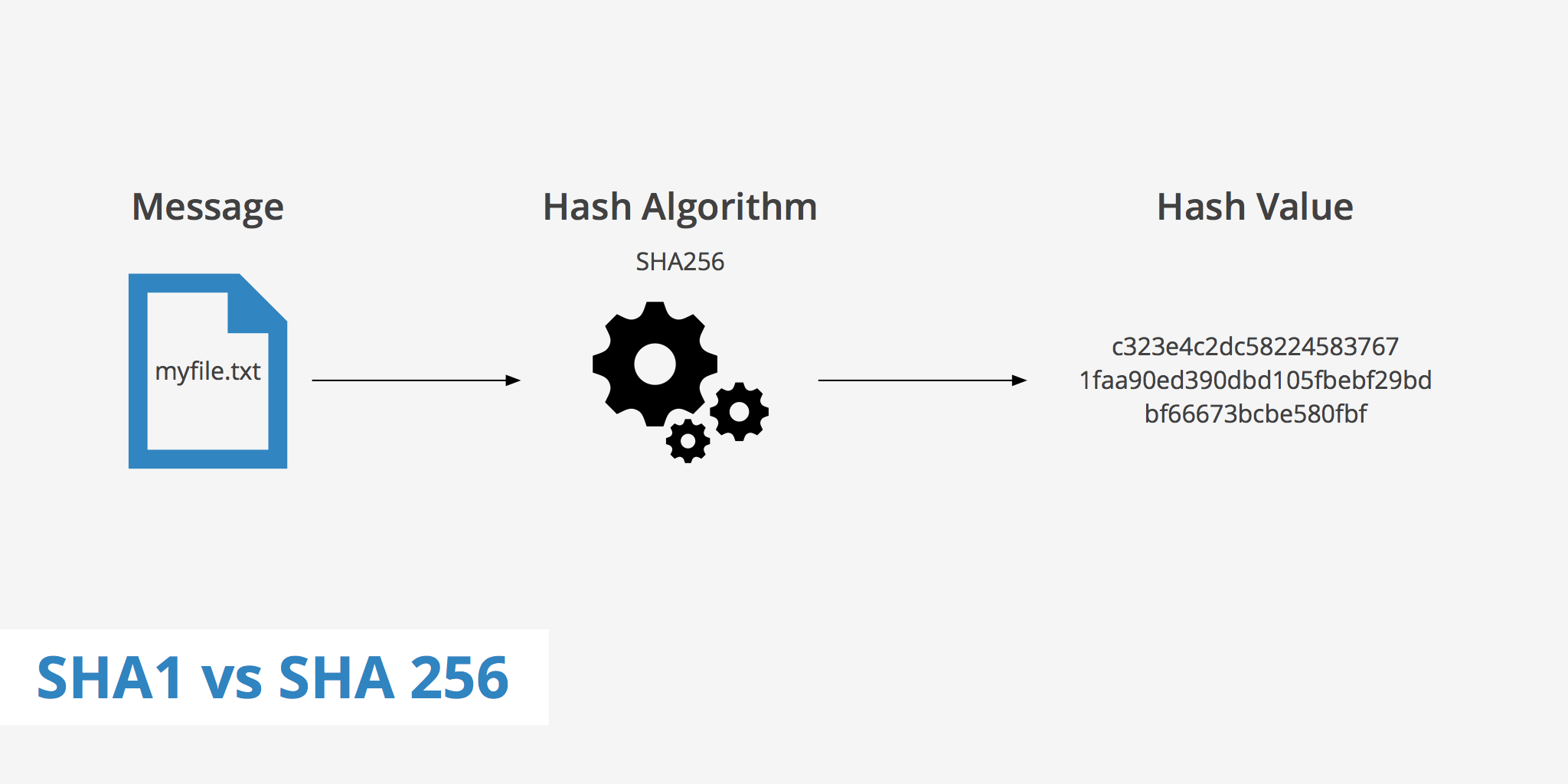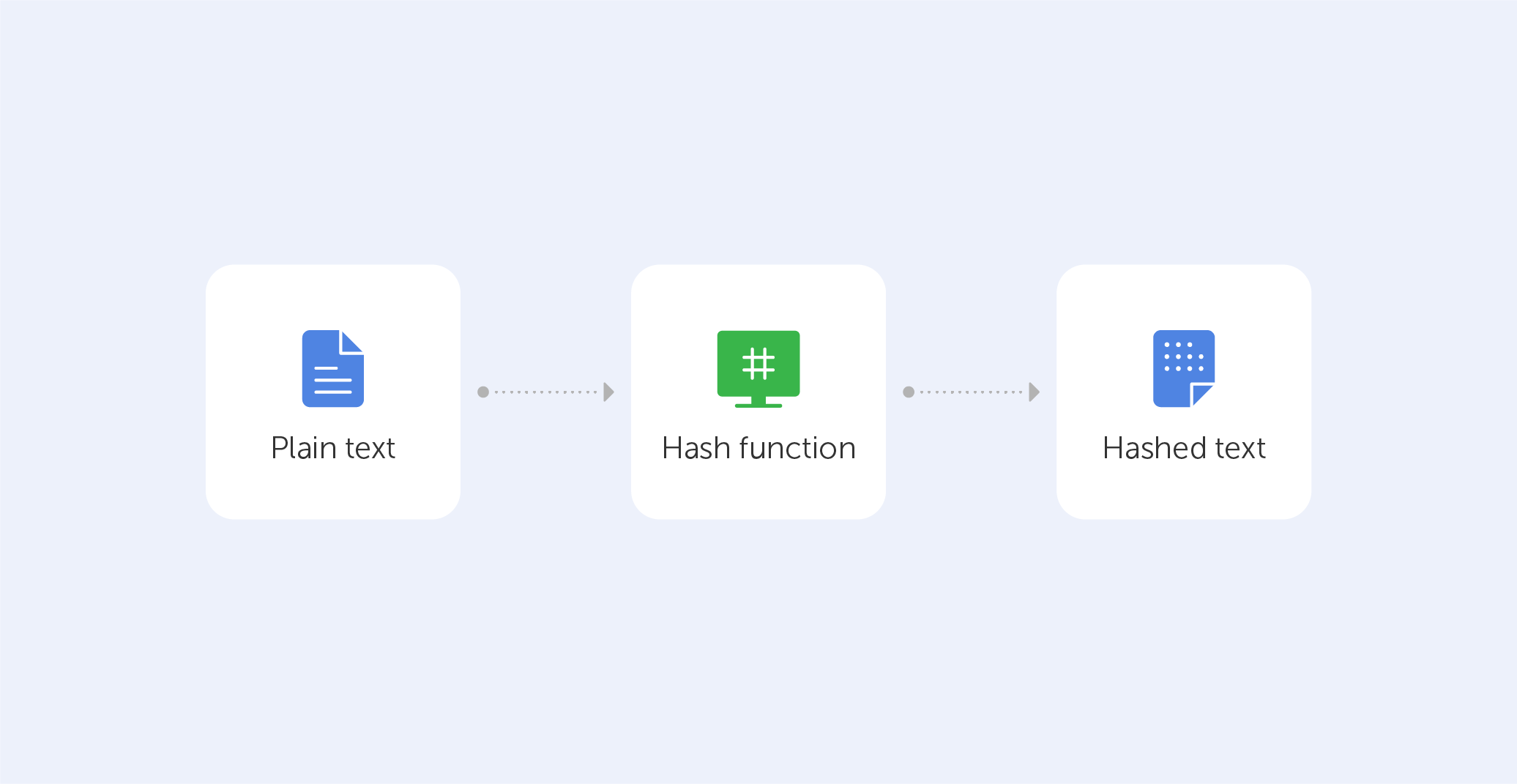
SHA-256 Animation' that allows you to intuitively understand the calculation process of the hash function 'SHA-256' with animation - GIGAZINE

SHA 256: Compute a SHA 256 hash using C# for effective security - .Net Core | MVC | HTML Agility Pack | SQL | Technology Crowds






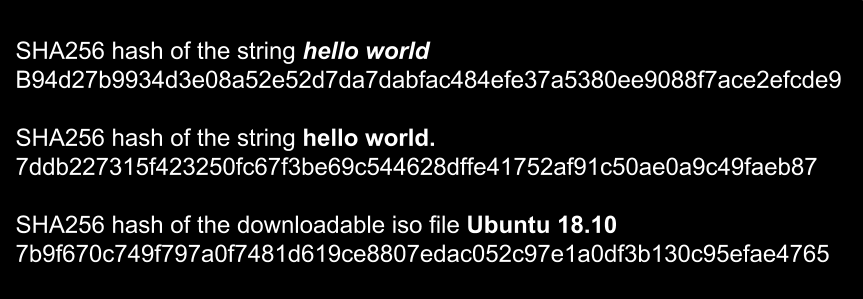






![Understanding the SHA256 hashing function - Learn Blockchain Programming with JavaScript [Book] Understanding the SHA256 hashing function - Learn Blockchain Programming with JavaScript [Book]](https://www.oreilly.com/api/v2/epubs/9781789618822/files/assets/c0859648-a484-478f-a7e0-75ce71d7340a.png)


![java] sha-256 해싱 알고리즘 사용하기 - 오오코딩 java] sha-256 해싱 알고리즘 사용하기 - 오오코딩](https://blog.kakaocdn.net/dn/cDoEMh/btre7IYsZDf/LgQkXZwATeqFm2pe8NBJk1/img.png)